HCP Vault Radar goes GA with Vault Import
HCP Vault Radar is now generally available to help organizations discover and prioritize unmanaged secrets, expanding on Vault’s secret lifecycle management capabilities. Accompanying GA is the ability to import unmanaged secrets discovered in collaboration platforms and Git-supported version control into HashiCorp Vault for centralized management.
Securing sensitive data in Vault, such as secrets, is crucial for protecting an organization's most valuable assets and ensuring that access to critical systems is tightly controlled. Securely storing secrets with Vault also presents the opportunity to transition unmanaged secrets to dynamic secrets or implement an automated rotation strategy that minimizes risks associated with credential exposure.
This post will explain the benefits of HCP Vault Radar and explore the details of its new unmanaged secret import feature.
Why HCP Vault Radar?
Verizon's Data Breach Investigations Report (DBIR) highlights the critical importance of detecting and resolving exposed credentials to safeguard organizational security. According to the 2025 report, 88% of web application attacks involve the use of stolen credentials. These findings emphasize that exposed or weak credentials serve as primary entry points for attackers, making it imperative for organizations to proactively detect and resolve such vulnerabilities to prevent unauthorized access and potential data breaches.
HCP Vault Radar helps DevOps and security teams reduce the risk associated with secret sprawl by detecting unmanaged and leaked secrets, as well as those that have been hard coded or reside in plaintext, so they can take appropriate actions to remediate these vulnerabilities. HCP Vault Radar scans for secrets like usernames and passwords, API keys, and tokens in popular developer tools and repositories. It then centralizes and displays that data in a prioritization portal and offers remediation options.
Inspect code at scale
HCP Vault Radar is a security tool designed to help organizations detect and prevent the accidental exposure of sensitive information, such as API keys, passwords, and other secrets, in their code repositories.
It uses advanced detection algorithms to identify hardcoded secrets in source code, configuration files, collaboration platforms, and other assets. It also integrates seamlessly with version control systems like Git, scanning current code repositories and new code submissions to provide real-time alerts and block commits containing sensitive information. By incorporating HCP Vault Radar into the development pipeline, organizations can ensure that secrets never make it into version control, minimizing the risk of data breaches and enhancing overall security practices within the software development lifecycle.
Broad data sources supported
At GA, HCP Vault Radar customers can scan the following data sources, with more continually being added:
- Git- version control systems (GitHub, GitLab, Bitbucket, Azure DevOps)
- Continuous integration and deployment (CI/CD) platforms
- Confluence
- JIRA
- AWS Parameter Store
- Server file directory structures
- Amazon S3
- Terraform
- Slack
Scan cloud-based, on-premises, and hybrid environments
HCP Vault Radar supports secret scanning from the HashiCorp Cloud Platform (HCP) as well as agent-based and command line interface (CLI) variants that allow for hybrid on-premises and self-managed scanning. Results from all sources are integrated into the HCP dashboard — this portal provides a streamlined prioritization and remediation user experience for secrets.
Scans initiated from the CLI tool are best for non-continuous or non-rule-based scans of a particular file or folder’s contents. Once the CLI scan is completed, the results can be uploaded to the HCP portal.
Prioritize risks effectively
Secret scanning is helpful only if it detects signals from noise. As a result, secret scanning tools should help you determine if exposed secrets are low-risk or significant threats. That’s why HCP Vault Radar has invested heavily in reducing false positives and helping users effectively prioritize remediation efforts.
HCP Vault Radar evaluates several factors to rank the severity of an exposed secret.
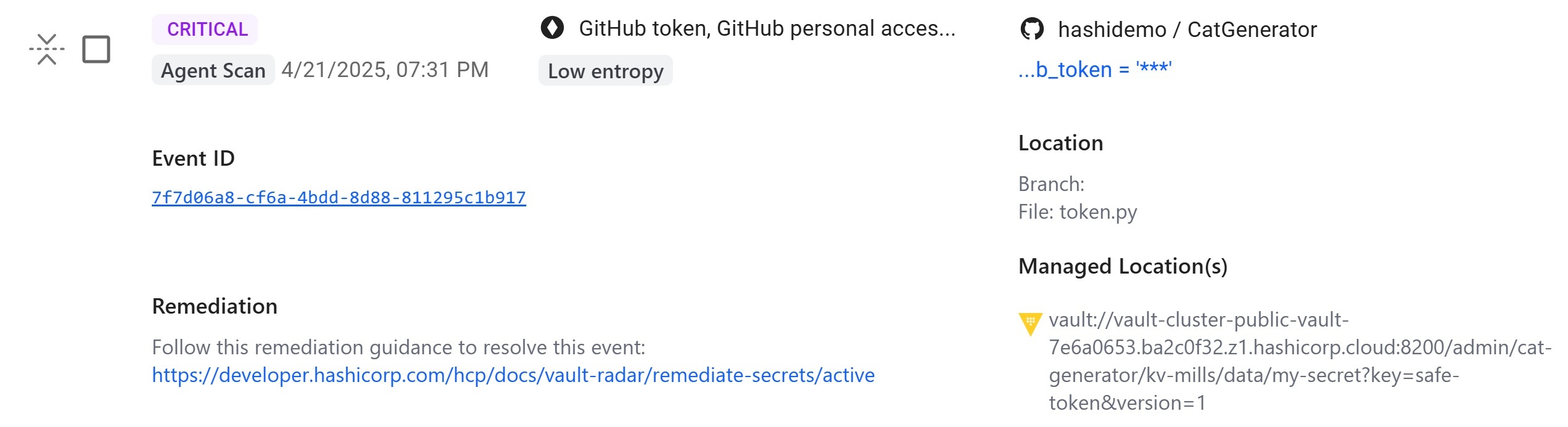
- Vault correlation in HCP Vault Radar checks if secrets detected in application environments were ever stored in HashiCorp Vault.. This enables teams to identify if previously secured secrets were mishandled by admins and require immediate attention..
- Version history analysis in HCP Vault Radar determines if a secret is newly introduced, longstanding, or already removed, which directly impacts risk assessment. A secret found only in the latest version typically signals an active, unmitigated exposure — elevating its criticality for remediation.
- When HCP Vault Radar finds a credential, it conducts activeness checks by calling out to the associated application to check if the secret is still active. The product can evaluate a wide array of secret types, including Google Cloud API keys, Amazon Web Services (AWS) credentials, GitHub personal access tokens, and JSON web tokens (JWT).
- Relying on pattern-matching text searches alone increases the risk of missing secrets that don’t adhere to a particular format. HCP Vault Radar entropy algorithms are highly effective at identifying random or complex strings that frequently indicate the content is a secret.
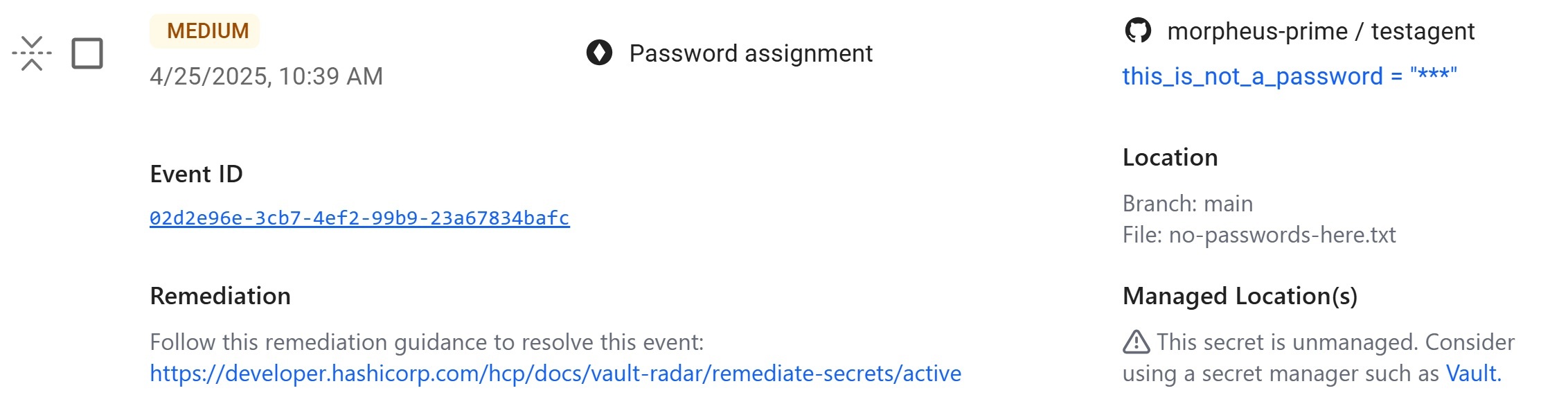
Guided remediation workflows
Security teams following best practices provide standardized recommendations to partner teams on how to remediate discovered secrets. To support their workflows, HCP Vault Radar natively provides contextual remediation guidance to users based on secret type. Native remediation guidance is provided for:
In addition to the native contextual guidance, HCP Vault Radar empowers security teams to add URLs that reference internally approved best practices and security policies to remediate a leaked secret.
Integrate incident management tools
In addition to secret scanning, HCP Vault Radar supports a robust set of remediation workflows via ticketing and alerting solutions. HCP Vault Radar includes integrations with the following alerting and ticketing solutions for further security incident response:
Import unmanaged secrets to Vault (New)
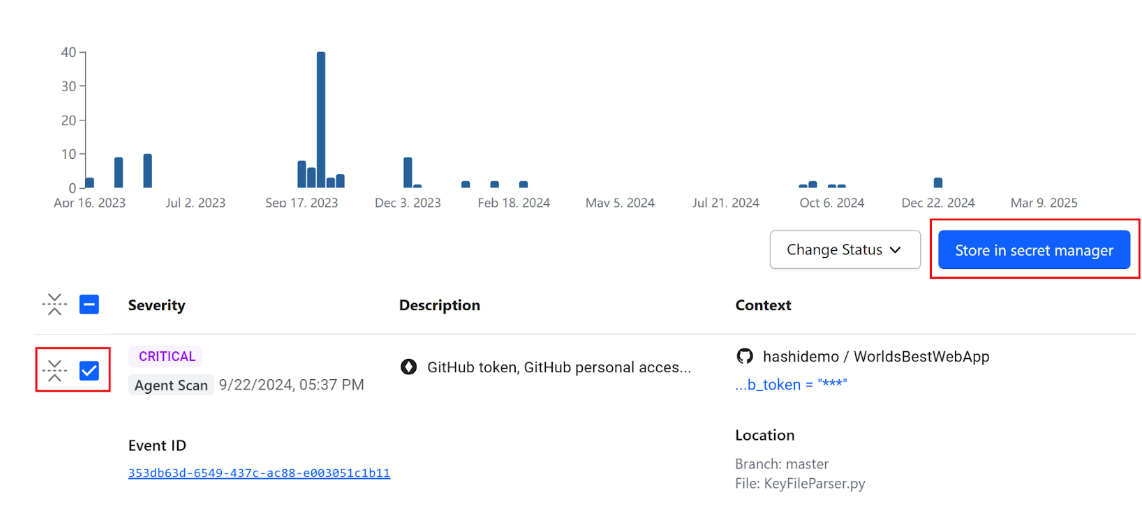
Finding and removing a discovered secret is only the first step in remediation. Organizations should securely store and provide controlled access to secrets using identity-based authentication and authorization.
With today’s release, HCP Vault Radar users can directly copy discovered secrets into HashiCorp Vault Dedicated or Vault Enterprise for secure ongoing management. By copying the secret from Radar to Vault, security teams expedite the remediation process and can rotate and revoke the offending secret once the source code is corrected.
Prevent exposed secrets
Preventing secrets from ever entering your codebase is one of the most effective ways to reduce security risk. By identifying and blocking exposed credentials early in the development process, organizations can avoid downstream vulnerabilities and costly incidents.
HCP Vault Radar utilizes pre-receive and pre-commit webhooks to evaluate pull requests and prevent the accidental exposure of sensitive information. These webhooks can be integrated within existing developer workflows to prevent the leakage of secrets at various stages of the pipeline. The pre-commit webhook is triggered before any changes are committed to version control, scanning the code locally for sensitive information.
If any secrets are detected, the commit is blocked, preventing sensitive data from being pushed to the repository. Meanwhile, pre-receive webhook scans code before being accepted by the repository, adding a layer of security at the push stage. Together, these webhooks ensure that no secrets make it into the codebase.
Learn more about HCP Vault Radar
HCP Vault Radar is a critical new addition to HashiCorp Vault’s security lifecycle management capabilities that helps enterprises reduce risk associated with credential exposure. Discovery of unmanaged secrets and subsequent remediation workflows further differentiate Vault’s secrets lifecycle management offerings by helping organizations take a proactive approach to remediating secret exposure before a data breach occurs.
To learn more, sign up for HCP Vault Radar’s free trial and check out these resources: